EnjOy :) MamoOn..
December 30, 2010
How to access sharing data offline
How to start windOws Xp faster
Start windows faster - Method:
Step 1:
Click the Start button in the lower-left corner of Windows.
Step 2:
Click Run.
Step 3:
A window opens.Type msconfig in the blank, and then click the OK
button or press the Enter key.
Step 4:
The System Configuration Utility window opens. Click the Startup
tab on the far right
.
Step 5:
In the Startup Item column on the left is a list of programs with
checkmarks next to them.A checkmark indicates
that the program is scheduled to launch each time Windows starts.To
prevent a program from loading at startup, remove the checkmark
from its box. Here are guidelines about which programs to allow or to
disable:
• Disable non-essential multimedia programs like qttask (which is
part of the QuickTime software), realsched (which is part of the
RealPlayer software), or Adobe Reader.
• Allow common processes for Windows and Microsoft Office.
• Allow programs related to your antivirus software, antispyware
software, or firewall. For example, if you use the ZoneAlarm fire-
wall and Spy Sweeper antispyware program, then you should
allow the startup programs named zlclient and SpySweeper.
• Allow programs related to your printer. For example, if you have
an Epson printer, then allow the startup program named Epson
Status Monitor.
Step 6:
If you are uncertain about whether or not to disable a particular program, do the following:
a. Write the program’s name on a piece of paper.
b. Connect to the Internet.
c. In your Web browser, type http://www.processlibrary.com to
visit the Process Library.
d. Near the top of this website’s main page is a Search for a Process
search box.Type the name of your program into this box, and
then click the Search Now button.
You are taken to a Web page that explains what your program is
used for and whether or not it is essential to your computer’s
performance.
Step 7:
7. When you have finished tweaking the System Configuration Utility,
click the Apply button.
Step 8:
8.Click the OK button.
Step 9:
9. A message alerts you that you must restart your computer for the
changes to take effect. Click the Restart button.Your computer auto-
matically shuts down and reboots.
Step 10:
When you return to Windows, a message alerts you that you have just
used the System Configuration Utility to change the way Windows
starts. Put a checkmark in the box labeled “Don’t show this message
or launch the system configuration utility when Windows starts.”
Step 11:
Click the OK button.
By following these steps you wil realize that your windows no starts faster.. EnjOy :) MamoOn..
Download any video from youtube for free widout ant sofrware

Here is the easiest way to download any video from Youtube.
While playing the video on youtube.com, Copy its location from the address bar like www.youtube.com/watch?v=sasad7657dms2
then add the word ‘kick’ between www. and youtube.com/link…….
EXAMPLE: www.kickyoutube.com/watch?v=sasad7657dms2
That’s it, Download without any other software or going to any other site, as their are many but this method is the best one according to me. Enjoy :) MamoOn..
December 29, 2010
Begniner's Guide To Hack Wirles Network
Basic Entry into a WEP Encrypted Network
This Tutorial explains EVERYTHING in detail So, it is quite long. Enjoy.
1. Getting the right tools
This Tutorial is in Bt3 But Download The Latest Release Bt4.
Download Backtrack 4. It can be found here:
http://www.backtrack-linux.org/downloads/
I downloaded the Dvd iso and burned it to a Dvd. Insert your BT4 Dvd/usb drive and reboot your computer into BT4. I always load into the 3rd boot option from the boot menu. (VESA/KDE) You only have a few seconds before it auto-boots into the 1st option so be ready. The 1st option boots too slowly or not at all so always boot from the 2nd or 3rd. Experiment to see what works best for you.
2. Preparing the slave network for attack
Once in BT4, click the tiny black box in the lower left corner to load up a "Konsole" window. Now we must prep your wireless card.
Type:
airmon-ng
You will see the name of your wireless card. (mine is named "ath0") From here on out, replace "ath0" with the name of your card.
Now type:
airmon-ng stop ath0
then type:
ifconfig wifi0 down
then:
macchanger --mac 00:11:22:33:44:55 wifi0
then:
airmon-ng start wifi0
What these steps did was to spoof (fake) your mac address so that JUST IN CASE your computeris discovered by someone as you are breaking in, they will not see your REAL mac address. Moving on...
Now it's time to discover some networks to break into.
Type:
airodump-ng ath0
Now you will see a list of wireless networks start to populate. Some will have a better signal than others and it is a good idea to pick one that has a decent signal otherwise it will take forever to crack or you may not be able to crack it at all.
Once you see the network that you want to crack, do this:
hold down ctrl and type c
This will stop airodump from populating networks and will freeze the screen so that you can see the info that you need.
**Now from here on out, when I tell you to type a command, you need to replace whatever is in parenthesis with what I tell you to from your screen. For example: if i say to type:
-c (channel)
then dont actually type in
-c (channel)
Instead, replace that with whatever the channel number is...so, for example you would type:
-c 6
Can't be much clearer than that...lets continue...
Now find the network that you want to crack and MAKE SURE that it says the encryption for that network is WEP. If it says WPA or any variation of WPA then move on...you can still crack WPA with backtrack and some other tools but it is a whole other ball game and you need to master WEP first.
Once you've decided on a network, take note of its channel number and bssid. The bssid will look something like this --> 05:gk:30:fo:s9:2n
The Channel number will be under a heading that says "CH".
Now, in the same Konsole window, type:
airodump-ng -c (channel) -w (file name) --bssid (bssid) ath0
the FILE NAME can be whatever you want. This is simply the place that airodump is going to store the packets of info that you receive to later crack. You don't even put in an extension...just pick a random word that you will remember. I usually make mine "wepkey" because I can always remember it.
**Side Note: if you crack more than one network in the same session, you must have different file names for each one or it won't work. I usually just name them wepkey1, wepkey2, etc.
Once you typed in that last command, the screen of airodump will change and start to show your computer gathering packets. You will also see a heading marked "IV" with a number underneath it. This stands for "Initialization Vector" but in noob terms all this means is "packets of info that contain clues to the password." Once you gain a minimum of 5,000 of these IV's, you can try to crack the password. I've cracked some right at 5,000 and others have taken over 60,000. It just depends on how long and difficult they made the password.
Now you are thinking, "I'm screwed because my IV's are going up really slowly." Well, don't worry, now we are going to trick the router into giving us HUNDREDS of IV's per second.
3. Actually cracking the WEP password
Now leave this Konsole window up and running and open up a 2nd Konsole window. In this one type:
aireplay-ng -1 0 -a (bssid) -h 00:11:22:33:44:55 ath0
http://i574.photobucket.com/albums/ss184...eplay1.jpg
This will send some commands to the router that basically cause it to associate with your computer even though you are not officially connected with the password. If this command is successful, you should see about 4 lines of text print out with the last one saying something similar to "Association Successful :-)" If this happens, then good! You are almost there. Now type:
aireplay-ng -3 -b (bssid) -h 00:11:22:33:44:55 ath0
http://i574.photobucket.com/albums/ss184...eplay2.jpg
This will generate a bunch of text and then you will see a line where your computer is gathering a bunch of packets and waiting on ARP and ACK. Don't worry about what these mean...just know that these are your meal tickets. Now you just sit and wait. Once your computer finally gathers an ARP request, it will send it back to the router and begin to generate hundreds of ARP and ACK per second. Sometimes this starts to happen within seconds...sometimes you have to wait up to a few minutes. Just be patient. When it finally does happen, switch back to your first Konsole window and you should see the number underneath the IV starting to rise rapidly. This is great! It means you are almost finished! When this number reaches AT LEAST 5,000 then you can start your password crack. It will probably take more than this but I always start my password cracking at 5,000 just in case they have a really weak password.
Now you need to open up a 3rd and final Konsole window. This will be where we actually crack the password. Type:
aircrack-ng -b (bssid) (filename)-01.cap
Remember the filename you made up earlier? Mine was "wepkey". Don't put a space in between it and -01.cap here. Type it as you see it. So for me, I would type wepkey-01.cap
Once you have done this you will see aircrack fire up and begin to crack the password. typically you have to wait for more like 10,000 to 20,000 IV's before it will crack. If this is the case, aircrack will test what you've got so far and then it will say something like "not enough IV's. Retry at 10,000." DON'T DO ANYTHING! It will stay running...it is just letting you know that it is on pause until more IV's are gathered. Once you pass the 10,000 mark it will automatically fire up again and try to crack it. If this fails it will say "not enough IV's. Retry at 15,000." and so on until it finally gets it.
http://i574.photobucket.com/albums/ss184...crack1.jpg
If you do everything correctly up to this point, before too long you will have the password! now if the password looks goofy, dont worry, it will still work. some passwords are saved in ASCII format, in which case, aircrack will show you exactly what characters they typed in for their password. Sometimes, though, the password is saved in HEX format in which case the computer will show you the HEX encryption of the password. It doesn't matter either way, because you can type in either one and it will connect you to the network.
Take note, though, that the password will always be displayed in aircrack with a colon after every 2 characters. So for instance if the password was "secret", it would be displayed as:
se:cr:et
This would obviously be the ASCII format. If it was a HEX encrypted password that was something like "0FKW9427VF" then it would still display as:
0F:KW:94:27:VF
Just omit the colons from the password, boot back into whatever operating system you use, try to connect to the network and type in the password without the colons and presto! You are in!
It may seem like a lot to deal with if you have never done it, but after a few successful attempts, you will get very quick with it. If I am near a WEP encrypted router with a good signal, I can often crack the password in just a couple of minutes.
I am not responsible for what you do with this information. Any malicious/illegal activity that you do, falls completely on you because...technically...this is just for you to test the security of your own network. :-)
I will gladly answer any legitimate questions anyone has to the best of my ability.
HOWEVER, I WILL NOT ANSWER ANYONE THAT IS TOO LAZY TO READ THE WHOLE TUT AND JUST ASKS ME SOME QUESTION THAT I CLEARLY ANSWERED. No one wants to hold your hand through this...read the tut and go experiment until you get it right.
There are rare occasions where someone will use WEP encryption with SKA as well. (Shared Key Authentication) If this is the case, additional steps are needed to associate with the router and therefore, the steps I lined out here will not work. I've only seen this once or twice, though, so you probably won't run into it. If I get motivated, I may throw up a tut on how to crack this in the future.
Hacking WEP wifi passwords
By MamoOn,,
How To Recover deleted or corrupt photos
DiskInternals Flash Recovery is a flash memory file recovery tool that restores all corrupted and deleted photographs or the ones that were lost due to hardware malfunction. This utility works even if a memory card was re-formatted.
Features:
• Easy Recovery Wizard.
• Can preview and recover JPEG, JPG, TIFF, BMP, PNG, GIF, TGA and other images.
• Can preview and recover RAW images:
• CRW - Canon Digital Camera Raw Image Format.
• CR2 - Canon Digital Camera Raw Image Format version 2.0.
• NEF - Nikon Digital SLR Camera Raw Image File.
• PEF - Pentax Raw Image Format
• RAF - Fuji CCD-RAW Graphic File.
• X3F - Sigma Camera RAW Picture File.
• BAY - Kodak/Roper Bayer Picture Sequence.
• ORF - Descent 3 Outrage Room Format.
• MRW - Minolta Diamage Raw Image File.
• RAW - Image Alchemy HSI Temporary Raw Bitmap
• SRF - Sony DSC-F828 Raw Image File.
• Other RAW images
• Works under Microsoft® Windows® 95, 98, ME, NT, 2000, XP, 2003 Server.
• Supported file systems: FAT12, FAT16, FAT32, NTFS (NT 4), NTFS5 (2000, XP).
• Recovered files can be saved on any (including network) disks visible to the host operating system.
• Creates recovery snapshot files for logical drives. Such files can be processed like regular disks.
Hack Facebook/Twitter Or Any Email Account With Session Hijacking
When logging into a website you usually start by submitting your username and password. The server then checks to see if an account matching this information exists and if so, replies back to you with a "cookie" which is used by your browser for all subsequent requests.
December 28, 2010
:: CREATE HIDDEN ADMIN ACCOUNT IN XP ::
Follow the Steps to Create Hidden admin Account in Windows XP
First Goto Start -> Run -> Type regedit -> Enter
In the Left Menu goto,
HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\SpecialAccounts\UserList*
In the Right pane, Right click -> New -> String Value
Right click on the new String Value and click Rename
Type the Name of the Account you want to hide.
Hit Enter then Right click on the String Value again and Change value to 0 which hides it. If you want it to be Visible to all Enter the Value 1.
Now Save and Exit the Registry and Logoff.
Goto welcome screen and Hit ctrl+alt+del twice to bring up Logon prompt
Type hidden Accounts name and password
Enjoy!!
HOW TO REMOVE OR EDIT WINDOWS SAVED PASSWORDS
Windows XP does not offer a very easy way to review or remove the saved passwordsthough. If you follow the steps below though you can access a graphical interface to add, remove or edit the saved passwords on a given system.
1. Click and select Run
2. In the Open field type "rundll32.exe keymgr.dll, KRShowKeyMgr"
3. Once the Stored Usernames and Passwords interface opens you can select any of the entries and select Properties to view the existing information
4. To remove a saved password you can select one of the entries and select Remove. A confirmation screen will appear. Click on OK and the account will be removed
5. You can add additional passwords as well by clicking on the Add button and entering the appropriate information
6. Repeat the steps above as needed to add, remove or edit saved passwords
7. When you are done using the interface click the Close button.
Firefox Addon For Easier Web Designing -"FIREBUG"
Monitor Network Activity
If the page taking time to load which maybe due to large images or JavaScript codes or partner's ads,you can go through each of the files and monitor which is taking more bandwith and so its taking time to load.
Quickly Find Errors
Firebug lets you know what errors are present on the web page and quickly let your fix it when you understand it because its easy y fix error once you get the actual problem.
::Faster Acrobat Reader ::
Is Acrobat Reader a little slow at loading in Microsoft Windows XP? Well here is how to speed it up!
Go to
C:\Program Files\Adobe\Acrobat 6.0\Reader(If you do not use drive C: as your hard drive, then change it to your hard drive)
Now create a new folder called
plug_ins_disabled
Now all you have to do is to move all your files from
plug_ins
To your new folder
plug_ins_disabled
But do not move these files:
EWH32.api, printme.api, and search.api
Ok so now you have all but 3 files in your plug_ins_disabled folder. Good job, you have just made Acrobat Reader load faster in Windows XP!
EnjOy.. :)
MamoOn..
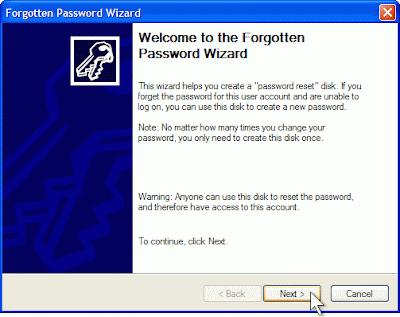
:: Password Recovery Disk ::
You should always take a good set of measures to prevent the loss of user level passwords.
Whether or not you remember a password in Windows, it doesn’t really matter. With Windows XP Wizard for forgotten password, your conscience will be free and clear – in case you accidently forgot your password.
I suggest that you create a restore disk with all of your passwords to your account. Why? Because creating a restore disk is simple with the following directions, and if you ever do forget your password, you will have it on a disk. This is a lot easier than any other way there is.
Proceed as follows to the Forgotten Password Wizard:
Simply click on the menu “Start, Control Panel, User Accounts.
Click on your user name.
Under Tasks on the left side, click “Prevent forgotten password” to start the wizard.
Now that you have wizard open, it will take you through the creation of the password restore disk. Make sure the disk is formatted and in your drive. Upon completion of the disk, label and store it somewhere in case of an emergency.
If you have forgotten your password, the only thing you need to do is click your user name in the connection icon on the screen. Even if you are don’t know your password, go ahead and click on the green arrow. It will open a small yellow dialog box that will direct you to use your password recovery CD.
:: Make Folders Invisible ::
Hiding folders is an easy to do task inMicrosoft Windows XP. This is a great way to keep all your personal files un-findable.
To do this, create a new folder some where. Then ‘Right Click’ and select
Rename
Now press and hold down the ‘Alt’ key and type in
0160
This will get rid of the text. Now ‘Right Click’ on the folder, and ‘click’ on
Properties
Now ‘click’ on the ‘Customize’ tab. Then click on
Change Icon
Scroll to the right until you find a few white icons. ‘Click’ on one of them, and then click on ‘Apply’ and then ‘Ok.’
You have just made a folder invisible and can hide all your personal files in it. Don’t you just love Windows XP?
:: How to surf web anonymously with TOR ::
Thus a proxy server hides our identity by acting as an intermediary between us and the web server that we are accessing. Suppose we break into a server using a proxy server thinking that we are anonymous. But what if owner of web server starts enquiring about the clients connecting to it using the proxy server and it is possible that owners of proxy server might reveal our identity. This means we cant actually rely on proxy servers for being anonymous online. Here comes the concept of THE ONION ROUTING (TOR) into picture. By using this , the client traffic is supposed to be passed from three different servers or nodes before reaching to actual web server. It may randomly take any path through any three nodes.
Lets consider it has taken path shown by green arrows. Now
* Node 1 knows only actual origin(client) but not actual destinantion(web server).
*Node 5 neither knows actual origin nor actual destinantion.
*Node 9 knows actual destination but not actual origin.
Thus no one exactly knows which client is accessing which web server. So it is highly anonymous.
Installing and Using TOR:
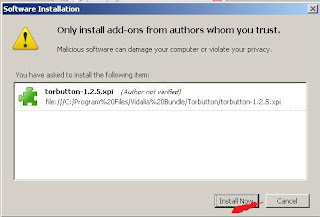
Step 1. Download the TOR client from the given link and run the setup .
http://adf.ly/BuiF
Note: You need to install a Mozilla firefox add on which is included in package you have downloaded to use Tor.
Step 2. Open the 'Vidalia Control Panel' from the task bar and Click on 'Start Tor'.
Step3. Now open Mozilla Firefox browser, single click on red highlighted 'Tor Disabled' on right corner of browser and it will turn to green highlighted 'Tor Enabled'.
Now just log on to 'www.whatismyip.com' and you will see your new public IP address that will keep changing after an interval of time according to the path randomly taken by web traffic through three different nodes.
:: Mobile Phone Spy Software ::
You can now easily find out who your partner, business associates, and friends have been in contact with. Whether you are suspicious of an affair, or would just like information that will help progress your career, you can now do all of the following using your mobile phone, and the person you are targeting will not suspect a thing. Guaranteed!
Ultimate Bluetooth Mobile Phone Spy Software Edition 2008 will work on All mobile devices that are bluetooth enabled. Not just phones but also laptops, computers, etc. YOU WILL RECEIVE SEPERATE SOFTWARE FOR OLD MODELS AND NEW MODELS (INCLUDING SYMBIAN PHONES). No need to list compatible phones - this works on ALL phones!
Not just 1 program but an entire suite that will work on old phones, new phones, smart phones, java phones - on absolutely all of them!
- VIEW CONTACTS LIST
- READ TEXT MESSAGES (SMS)
- VIEW CALLS MADE / CALLS RECIEVED
- SET THE TARGET PHONE TO CALL YOU WHENEVER IT MAKES OR RECEIVES A CALL
- VIEW PHOTOS